Once security roles have been created and constraints are applied to the role, users must be added to the role. This can be done by adding individual users to a role or by adding a particular OU or group to a role.
- Manual Assignment of Users - Users can be added manually to give a particular user permissions
- Dynamic Assignment of OUs or Groups - Users can be added dynamically, where the system automatically assigns a role based on set criteria. For example, all users in a position can be added to a security role. As soon as a user meets the selected criteria, they are added to the security role. Also, a security role can be assigned to a dynamic group, in which the group criterion dynamically assigns users to the group.
To add or remove users in a security role, go to . Next to the appropriate security role, select the Users icon ![]() . Then, select the Add Users or Remove Users link.
. Then, select the Add Users or Remove Users link.
Troubleshooting Note: The Add Users icon is only available for security roles that are not system-defined, such as the Manager role. Any security role that is system-defined is automatically managed by the system. For example, a user is automatically added to the Manager role if they are listed in the Manager role for at least one user. Users cannot be manually added to the Manager role from Security Role Administration.
| PERMISSION NAME | PERMISSION DESCRIPTION | CATEGORY |
| Security Administration - Manage | Grants ability to create, modify and constrain security roles within the portal, and assign users to those security roles. This permission can be constrained by OU, User's OU, User, and User Self and Subordinates. This is an administrator permission. | Core Administration |
Role Details
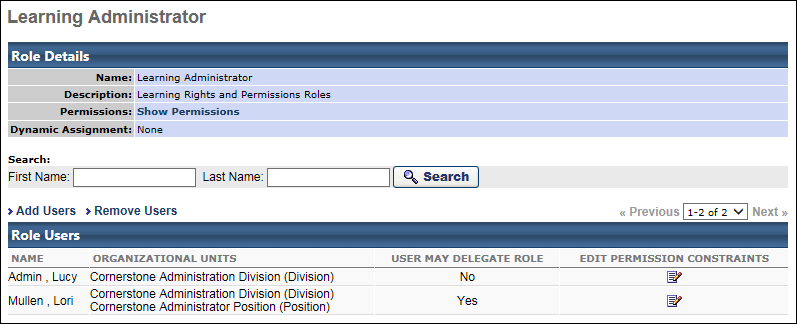
The following information is displayed in the Role Details section:
- Name
- Description
- Permissions - Click the Show Permissions link to view the permissions contained within the role.
- Dynamic Assignment - If the security role is dynamically assigned, the dynamic assignment criteria is displayed here.
- To remove the dynamic assignment criteria, click the Delete icon
 next to the criteria. This removes all users who were previously included in the dynamic assignment and also prevents new users from being dynamically assigned. This does not affect users who were added outside of the dynamic assignment criteria that was removed.
next to the criteria. This removes all users who were previously included in the dynamic assignment and also prevents new users from being dynamically assigned. This does not affect users who were added outside of the dynamic assignment criteria that was removed.
- To remove the dynamic assignment criteria, click the Delete icon
Add Users
To add user to a security role, go to . Next to the appropriate security role, select the Users icon ![]() . Then, select the Add Users link. The Add Role Assignment page opens.
. Then, select the Add Users link. The Add Role Assignment page opens.
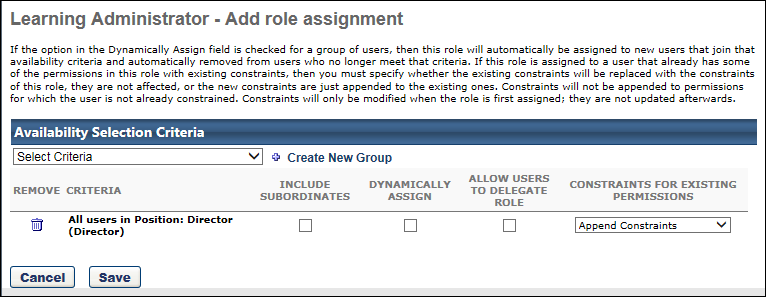
From the Select Criteria drop-down in the Availability Selection Criteria section, select the appropriate option, based on the type of assignment:
- To add all users to the role, select All Users.
- To add individual users to the role, select Users. Then click the Select icon to select the appropriate users.
- To add an OU or group to the role, select the appropriate OU type. Then click the Select icon to select the appropriate OUs or groups. Groups can be a useful way to assign security roles. See Use Groups to Assign Security Roles.
The following options are available for each selected user, OU, or group.
- Include Subordinates - Select this option to include subordinates. If a user is chosen, subordinates will include the user's direct reports. If an organizational unit is chosen, subordinate will include the selected OU's child OUs.
- Dynamically Assign - Select this option to allow a role to be automatically assigned or removed. This may be appropriate when assigning the security role to an OU or group. If this option is selected, every person who meets the criteria set is automatically assigned to the role as soon as they meet the criteria. When this option is selected, the following is true:
- If a new user is created who matches the criteria, they are assigned to the security role.
- If a user is added to an OU and meets the criteria, they are assigned to the security role.
- Users are not actually assigned to the security role until they log in to the system. The administrator will not see that the user has been assigned to the security role until the user logs in to the system. This includes the security role's list of assigned users and when viewing the user's permissions via User Record Administration.
- Important Note: If this option is not selected, then only the users who match the assignment criteria are assigned to the security role and those users are only removed if they are manually removed.
- Allow Users to Delegate Role - Select this option to allow users who are assigned this role to add other users to the security role. If this option is selected, users who are assigned this role must also have access to Security Role Administration to delegate their role.
- Important Note: If this option is not selected for a user, the user does not have access to the Add Users or Remove Users links for this role or any subsequent child roles. This also applies to users in the System Administrator role. To enable this, remove and re-add the user from the role and select this option prior to saving.
- Constraints for Existing Permissions - This option determines what the system does if the user who is assigned this role already has one or more of the permissions contained in this role and those permissions have constraints. Because users can be in many different security roles, a user may already have one or more of the permissions that are being granted to them. In this situation, the system needs to know which constraints should be applied. See the Constraints for Existing Permissions Example section below for additional information.
- Append Constraints - Add all the constraints from all the roles together. This option will add the constraints from this role to any constraints the user already has for the same permissions in another role.
- Replace Constraints - Keep only the new constraints. This option will replace the constraints set for the same permission in other roles with the constraints set for the permission in this role.
- Do Not Modify Constraints - Keep only the old constraints. This option will not change the constraints a user has in another role. However, any new permissions which the user does not already have will receive the constraints defined for those permissions for this role.
Click .
Remove Users
To remove users from a security role, go to . Next to the appropriate security role, select the Users icon ![]() . Then, select the Remove Users link. The Remove role assignment page opens.
. Then, select the Remove Users link. The Remove role assignment page opens.
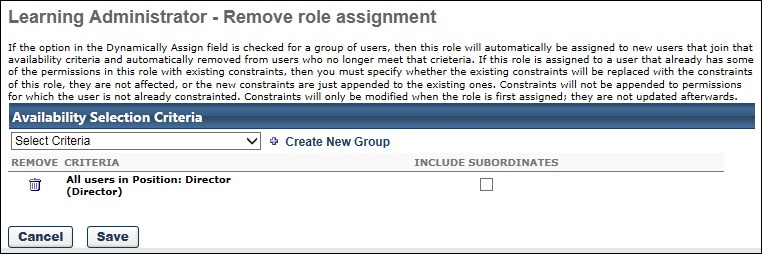
From the Select Criteria drop-down in the Availability Selection Criteria section, select the appropriate option, based on the type of assignment:
- To remove all users from the role, select All Users.
- To remove individual users from the role, select Users. Then click the Select icon to select the appropriate users.
- To remove an OU or group from the role, select the appropriate OU type. Then click the Select icon to select the appropriate OUs or groups.
The following options are available for each selected user, OU, or group.
- Include Subordinates - Select this option to include subordinates. If a user is chosen, subordinates will include the user's direct reports. If an organizational unit is chosen, subordinate will include the selected OU's child OUs.
Troubleshooting
For use cases that demonstrate how permission constraints are calculated when a user's permission constraints are merged between multiple roles or permissions, See Permission Constraint Calculation Use Cases.
Constraints for Existing Permissions Example
A user is in Security Role A, which has the permission to view user records. This permission is constrained to the Sales division.
The user is added to Security Role B, which also has the permission to view user records. In this role, this permission is constrained to the HR division.
The following scenarios may occur:
- Append Constraints - The constraints from Security Role B are appended to the user's previous constraints. The user now has permission to view user records for users in the Sales division and the HR division.
- Replace Constraints - The constraints from Security Role B replace the user's previous constraints. The user now has permission to view only user records for users in the HR division.
- Do Not Modify Constraints - The user's previous constraints are unaffected and the constraints from Security Role B are disregarded. The user has permission to view only user records for users in the Sales division.
See Permission Constraint Calculation Use Cases.