From the Users page, administrators can proxy into the system as another user, which enables the administrator to perform actions and test system behavior on behalf of the user. Important Note: Although the system tracks when administrators proxy as another user, the system does not track the actions that are performed by the administrators on behalf of the user.
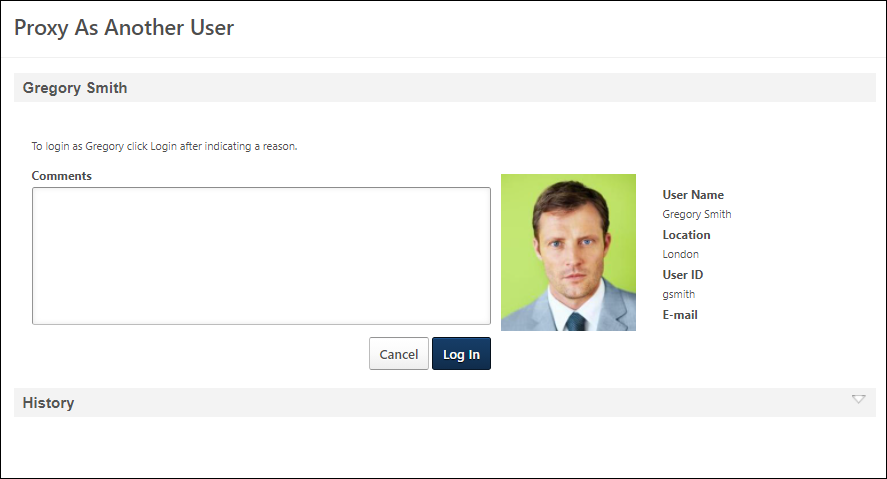
The Proxy as Another User page is the gateway for administrators to proxy in to the system as another user. This page enables the administrator to log in to the system as another user. In addition, this page provides a history of each time an administrator logs in to the system as the user.
To access the Proxy as Another User page, go to . Then, select the Proxy as User option in the Options drop-down menu for the appropriate user. Note: This option is not available if the user does not have a User ID set on their User Record.
| PERMISSION NAME | PERMISSION DESCRIPTION | CATEGORY |
User's Information
On the right side of the page, the user's photo is displayed along with their first name, last name, location, User ID, and email address. This information is pulled from their user record.
Proxy History
At the bottom of the page, the History section displays the details for each time an administrator logs in as the selected user. The History only applies to the selected user. All administrators that have access to the Proxy as Another User page can view the history for all other administrators that have logged in as the selected user
- Action Performed By - This displays the administrator that used the Proxy function to log in to the system as the user.
- Proxy Start Date and Time - This displays the date and time at which the administrator initially logged in as the user.
- Proxy End Date and Time - This displays the date and time at which the administrator's proxy session ended. This field remains blank if the administrator does not click the Log Out link within the user's system. This also applies if the administrator is automatically logged out because of another user logging in as the user.
- Reason for User Emulation - This displays the reason that the administrator provided when they logged in as the user.
Log In as User
To log in to the system as the user, follow these steps:
- In the Comments field, enter the reason for logging in to the system as the user. This reason should be descriptive so that other users understand the reason for the action. The character limit for this field is 500 and this field is required.
- After entering the comment, select the button. A confirmation pop-up appears.
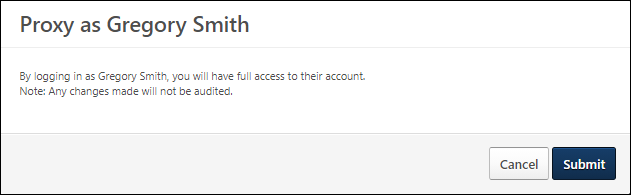
- Read the warning and select to log in as the user or select to cancel the attempt.
- When you log in as another user, a new browser window is opened in which you are logged in as the user. You remain logged in as yourself in the original window, which enables you to perform actions as yourself in the original window and to perform actions as the selected user in the new window.
- When you log in as the user, anyone else that is logged in to that account, including the user, is logged out of the account. Similarly, if another administrator or the user log in to the account, you are automatically logged out of the account.
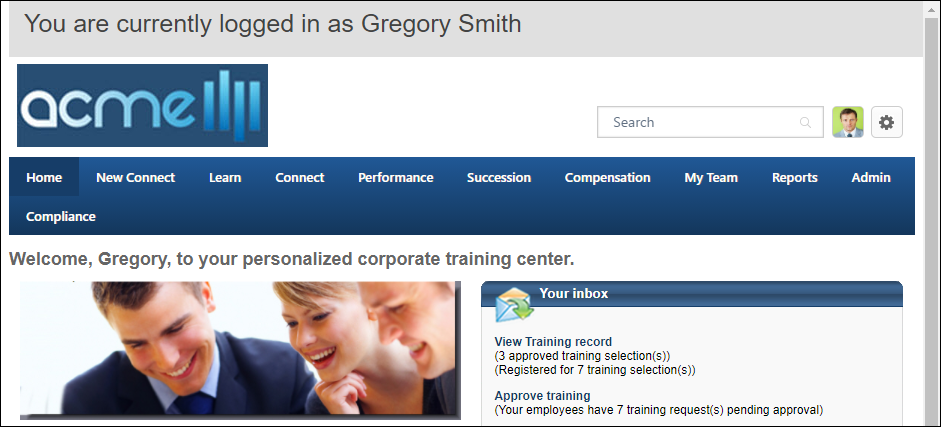
- After performing the necessary actions, select the Log Out option in the new window.
Proxy as Another User - Sensitive Personally Identifiable Information
When an administrator logs in to the system as another user using the Proxy as Another User functionality, that administrator can never unmask, edit, or set Sensitive Personally Identifiable Information (SPII) fields. This ensures the information is completely secured and can only be accessed by administrators who have the appropriate permissions.
If an administrator attempts to unmask or edit SPII fields, a pop-up opens to indicate that the administrator cannot access SPII fields when a use account is impersonated. If an administrator attempts to create a user and set SPII fields, an error message is displayed when the administrator attempts to save the user record.
In order to be able to unmask, edit, or set SPII fields, an administrator with the appropriate permissions must log in to the system or use Single Sign On (SSO) to log in as themselves.
Proxy as Another User - Launching Content
When trying to launch content while proxying as another user, some courses will restrict the user's access.
This is a security measure taken by some of the course providers when the launch is made from a different user context such as the one used when proxying as another user.